
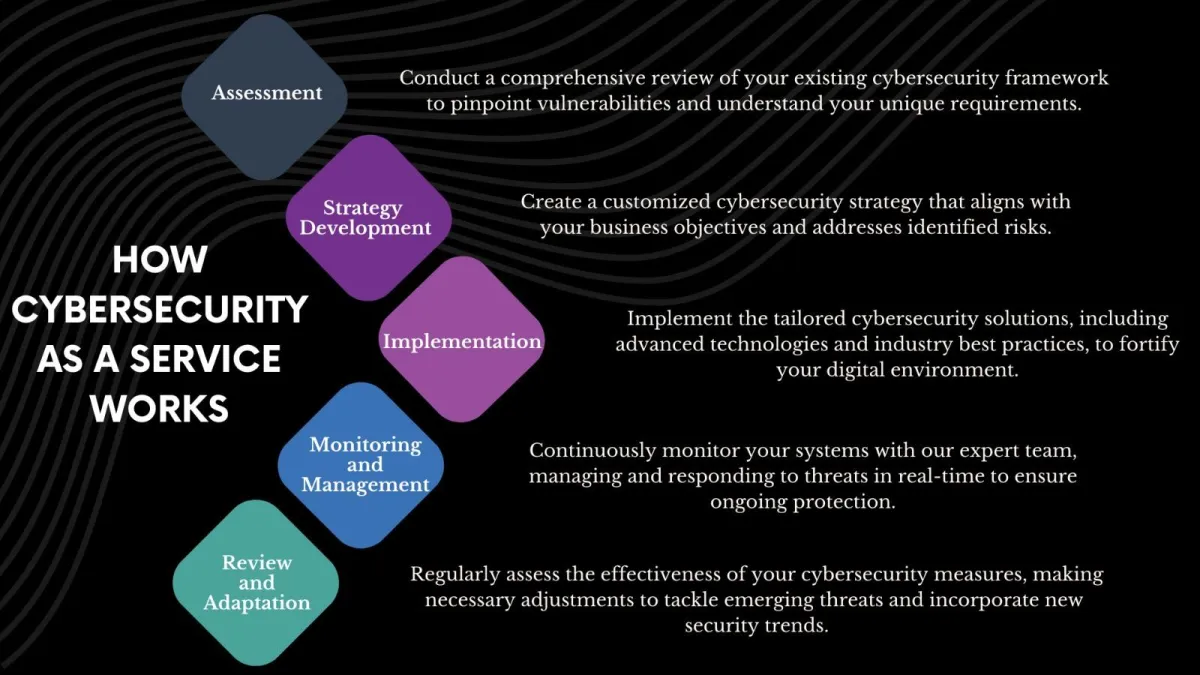
Cybersecurity as a Service
Cybersecurity as a Service offers businesses a dynamic shield
against digital threats, providing expert-led security management without
the complexity of in-house operations. It ensures continuous,
proactive monitoring and rapid response to vulnerabilities and attacks.
Cybersecurity Risk Assessment
Begin building a resilient cybersecurity posture with an in-depth
Cybersecurity Risk Assessment. Discover
your current protections, uncover critical vulnerabilities,
and learn your next strategic moves to enhance security.
Our mission is to help manage and mitigate the Cyber Security Risks of businesses,
safeguarding their operations, reputation, finance, and sensitive data.
Tekdana stands at the forefront of defense,
offering Cybersecurity as a Service to
navigate the intricate web of modern threats
from ransomware to AI vulnerabilities.
Our dedicated team empowers
your business with a robust security framework,
providing 24/7 proactive surveillance and response,
to safeguard your growth and continuity in the ever-evolving
cybersecurity landscape.

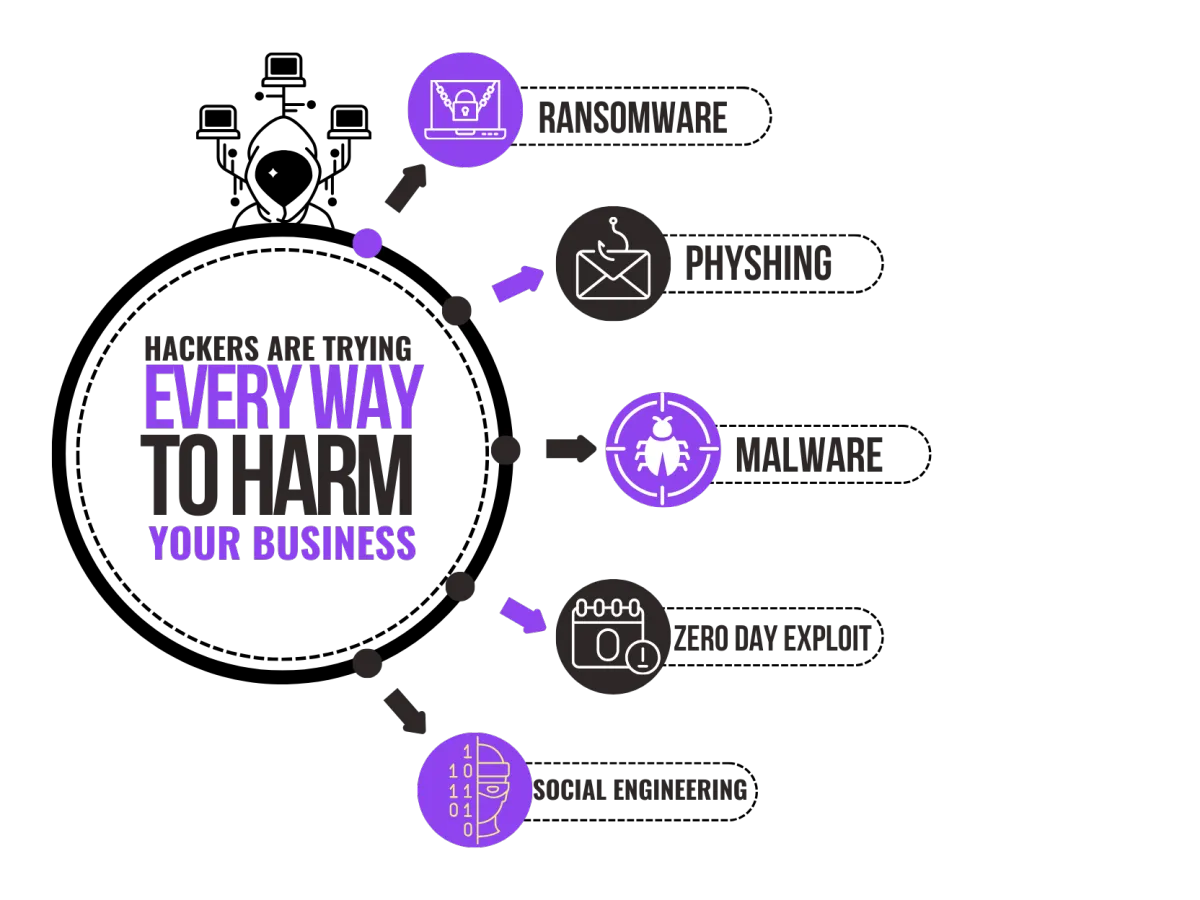
HACKERS ARE TRYING
EVERY WAY TO HARM YOUR BUSINESS
YOU MIGHT BE THINKING
I DON’T NEED IT NOW OR I WILL TRY THIS LATER
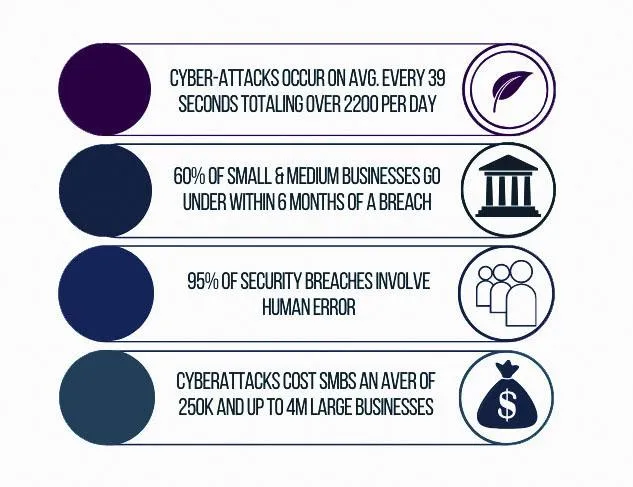
You are exactly what the Hackers want! They will attack small businesses more than large corporations just because we are busy building the Business!
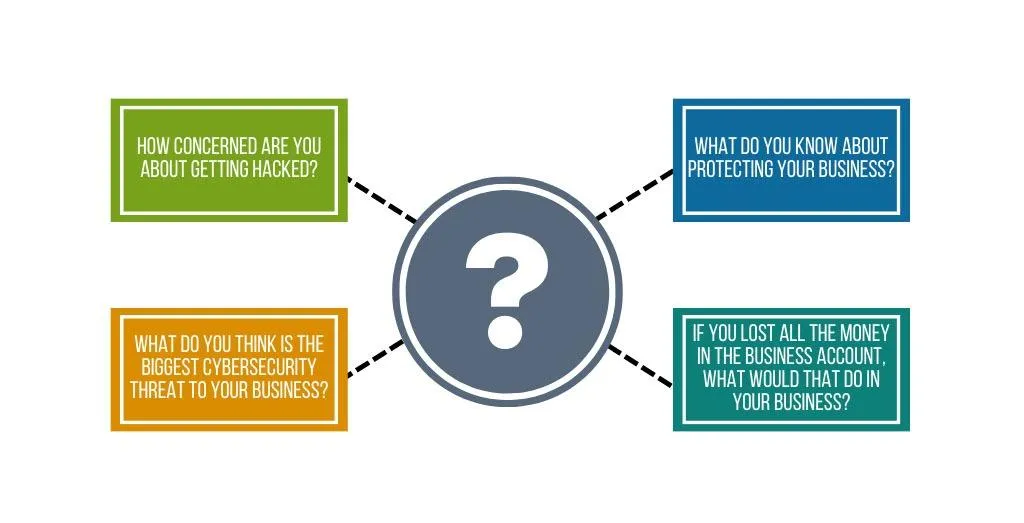
Do you want to protect your brand from Hackers?

FOR DETAILED INSIGHTS VISIT OUR BLOG
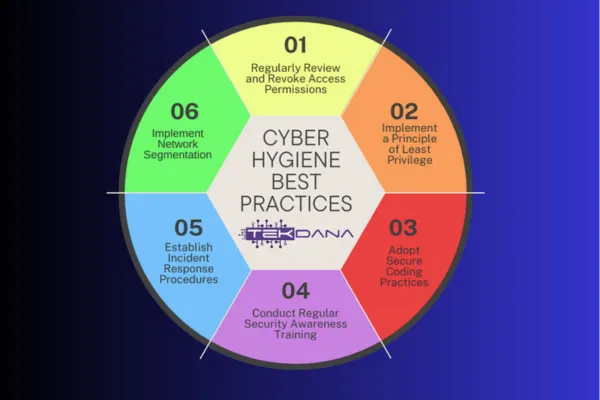
Cyber Hygiene Best Practices for Businesses
Cyber Hygiene Best Practices for Businesses
Essential Security Practices for Protection & Continuity. Disable AutoRun, implement web filtering, monitor network traffic, secure devices, and conduct security awareness training

Cyber hygiene refers to the practices and measures taken to maintain good cybersecurity. For businesses, it is essential as it protects sensitive data, preserves critical systems, and mitigates the risk of cyber attacks. By implementing strong passwords, updating software, and educating employees, businesses can reduce the likelihood of breaches. Below, we provide some key points of best practices to enhance your cyber hygiene.
Disable AutoRun/AutoPlay:
AutoRun and AutoPlay features, commonly found on operating systems, can automatically execute files from removable media such as USB drives. By disabling these features, you can prevent malware from spreading through unauthorized execution. This simple step significantly reduces the risk of malware infections and unauthorized access to your systems.
Implement Web Filtering:
Web filtering tools provide an additional layer of defense by blocking access to malicious or compromised websites. By carefully controlling internet access and filtering out potentially harmful content, you can minimize the risk of employees inadvertently visiting malicious sites that distribute malware or engage in phishing attacks.
Regularly Monitor Network Traffic:
Monitoring network traffic in real-time allows you to identify any unusual or suspicious activity that may indicate a malware infection or unauthorized access attempt. By leveraging network monitoring tools, you can detect and respond to potential threats promptly, mitigating their impact and preventing data breaches or system compromises.
Implement Application Whitelisting:
Application whitelisting is a proactive security measure that allows only authorized and trusted applications to execute on your company's systems. By explicitly defining a list of approved applications, you can prevent malicious software or unauthorized programs from running, significantly reducing the risk of malware infections and unauthorized system modifications.
Secure Mobile Devices:
Mobile devices have become an essential part of business operations, but their portability also makes them vulnerable to cyber threats. Implementing strong security measures on mobile devices, such as enforcing strong passcodes, enabling device encryption and using reputable security apps, helps protect sensitive company data and prevents unauthorized access in case of loss or theft.
Conduct Security Awareness Training:
One of the most critical aspects of cyber hygiene is educating employees about the risks they face and the best practices they should follow. Regular security awareness training sessions help employees recognize potential threats, such as phishing emails or suspicious websites, and empowers them to take appropriate actions to protect company data. By fostering a culture of cybersecurity awareness, you can significantly reduce the likelihood of successful cyber attacks.
Implementing these key points, businesses can significantly enhance their cybersecurity defenses. However, it's important to remember that cyber hygiene is an ongoing process that requires constant vigilance and adaptation to emerging threats. By consistently practicing good cyber hygiene, businesses can protect their digital assets, maintain customer trust, and ensure the continuity of their operations in an increasingly interconnected world.
Take The First Step Towards Cyber Resilience
Get A Security Assessment Today!
Stay in the know, subscribe to our Newsletter.

SITEMAP
Solutions
Cloud Services (CSP)
Professional Services
Products
TekDana. All rights reserved 2024. Privacy Policy